Shingeki no RSA
One encryption, three params, you know what to do.
https://drive.google.com/file/d/1xbwFfAHu5OWbkEV3QlYGP59nHXpv57WT/view?usp=sharing
题目给了一个out.txt,里面包含n,e,c的值
使用rsa-wiener-attack破解得到d的值
~$ python RSAwienerHacker.py
Hacked!
50954488565980029757584514143249292352586758895690937600871123296191815851393
代码:
from Crypto.Util.number import long_to_bytes
import gmpy2
e = 573539981054118375159951884901136205381955275096471242113613923667834312363548126598981740314307696033323138227176735824259098674326069670063001503892366653022633390483272968412233602239104757299239510751275655288670147128536527296060843927282827574422039154045360669647002461865276005609405093376965933104257
n = 666012509503758414438426745752029036046328310944346357068259451859585174290580664150188141697939659811599336002592599704089746160399428670863696780761420173279676565150259812749267725206078003773597631925996185977321417456827136083352043009732414371490356153874019687554196902819696964658218055292422529903061
c = 208271638964220806986932660131544686073844142913497222151993342727885811478884727510239109595118929917803309949401762080874858518281133929171859315997601484068462684780596513932104673255797873067799046024798017005908221308124294210078684387266545107254593378287958436606968619452939117043031695740389528821956
d = 50954488565980029757584514143249292352586758895690937600871123296191815851393
m = gmpy2.powmod(c, d, n)
print(long_to_bytes(m))
flag:SBCTF{d1d_y0u_us3_w13n3r's?}
Happy Flag
We have many flags. But we need a good flag!
https://drive.google.com/file/d/1194sBi8Ijb4C-cYDGP2qZvXgj9uxSe7R/view?usp=sharing
题目给了一个文件world_flags.zeep,file后发现是一个zip压缩文件,使用unzip解压.
解压后发现有
~$ file world_flags.zeep
world_flags.zeep: Zip archive data, at least v1.0 to extract
~$ unzip world_flags.zeep
Archive: world_flags.zeep
creating: world_flags/
inflating: world_flags/1.txt
inflating: world_flags/10.txt
inflating: world_flags/100.txt
inflating: world_flags/1000.txt
inflating: world_flags/10000.txt
inflating: world_flags/10001.txt
....
直接cat所有文件,然后用uniq去重
~$ cat *.txt | uniq
SBGTF{false_flag_🥺}
SBCTF{Cool_flag_!!!}
flag:SBCTF{Cool_flag_!!!}
Query The Flag
Query the flag
https://drive.google.com/file/d/1pwr09e-BoNoJujrJJ_hlAuhEGgJnsb6V/view?usp=sharing
题目给了一个SQLite的数据库文件,直接grep
~$ strings find.db | grep SBCTF
SBCTF{I_w@s_s0_sl33py_D3s1gn1ng_7h1s}NULL
flag:SBCTF{I_w@s_s0_sl33py_D3s1gn1ng_7h1s}
they all look the same
They are slightly different
https://drive.google.com/file/d/1XjkSCEjydggD7FHaWsBxKYTrivyesd1M/view?usp=sharing
解压下载的zip文件,发现里面一堆jpg文件,首先看看md5值
~$ md5 *
MD5 (images - Copy (1).jpg) = b69410fdc3f11fbac6bb3e32e40df1de
MD5 (images - Copy (10).jpg) = 1aa6e81b2335fdee91492125d4352503
MD5 (images - Copy (100).jpg) = 58d55ebd6b5b7717ec7188af4f4bef66
MD5 (images - Copy (101).jpg) = 58d55ebd6b5b7717ec7188af4f4bef66
MD5 (images - Copy (102).jpg) = 592434721909e841870ba0cfc0bce6aa
MD5 (images - Copy (103).jpg) = 58d55ebd6b5b7717ec7188af4f4bef66
MD5 (images - Copy (104).jpg) = 58d55ebd6b5b7717ec7188af4f4bef66
MD5 (images - Copy (105).jpg) = 58d55ebd6b5b7717ec7188af4f4bef66
然后用exiftool查看文件的元数据试试
~$ exiftool images\ -\ Copy\ \(1\).jpg
ExifTool Version Number : 12.31
File Name : images - Copy (1).jpg
Directory : .
File Size : 16 KiB
File Modification Date/Time : 2021:11:21 00:21:28+08:00
File Access Date/Time : 2021:12:10 09:32:26+08:00
File Inode Change Date/Time : 2021:12:10 09:32:26+08:00
File Permissions : -rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : inches
X Resolution : 96
Y Resolution : 96
Exif Byte Order : Big-endian (Motorola, MM)
Image Description : S
XP Title : S
Padding : (Binary data 2060 bytes, use -b option to extract)
About : uuid:faf5bdd5-ba3d-11da-ad31-d33d75182f1b
Title : S
Description : S
Image Width : 376
Image Height : 134
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 376x134
Megapixels : 0.050
发现Image Description里有一个S,顺序打印一下所有文件的Image Description试试
~$ for i in `seq 1 153`;do exiftool images\ -\ Copy\ \(${i}\).jpg| grep "Image Description";done
Image Description : S
Image Description : B
Image Description : C
Image Description : T
Image Description : F
Image Description : {
Image Description : H
Image Description : 0
Image Description : w
....
~$ cat tmp | awk '{print $4}' | xargs echo
S B C T F { H 0 w _ c 0 u l d _ y 0 u _ d ! s t ! n g u ! s h S _ S S S ! S S S m S S S @ S S S g S S S 3 S S S s S S S _ S S S
结尾似乎有一些多余的S,去掉后即可得到flag
flag:SBCTF{H0w_c0uld_y0u_d!st!ngu!sh_!m@g3s_}
Discord
Find the account creation date of one of our discord channel admins (4dam).
Note: Please put the date in this format YYYY/MM/DD for submission, like this: SBCTF{1970/01/01}
题目要求我们找到管理员4dam创建账号的时间.
首先打开Discord->:gear:->高级设置,打开“开发者模式”
对着头像右键,复制ID(808684903301775360)
打开https://snowsta.mp,输入ID查询
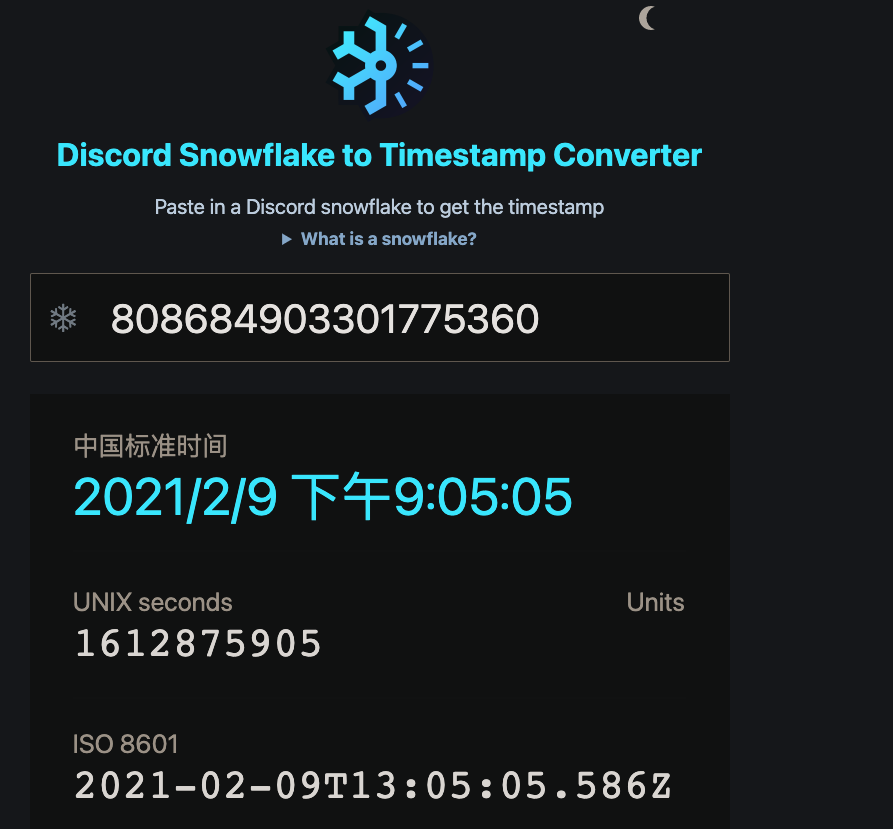
flag:SBCTF{2020/02/09}
Email Hunt
I want to find the PGP Public Key of someone's ProtonMail account, but all I got is a useless document he shared with me (https://docs.google.com/spreadsheets/d/1iBRs347v5xXICdgHm4-sQBEFozbqhTABPIespxSBI20).
Can you help me find it?
Note: Please submit the flag like this example:
-----BEGIN PGP PUBLIC KEY BLOCK-----
Version: ProtonMail
aBBBBBBBBBBBBBBBB
BBBBBBBBBBBBBBBBB
BBBBYz
-----END PGP PUBLIC KEY BLOCK-----
Flag: SBCTF{aBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBYz}
访问题目中给出的Google表格的链接.
然后访问https://docs.google.com/spreadsheets/u/0/查看最近访问的表格文件,并用F12抓包
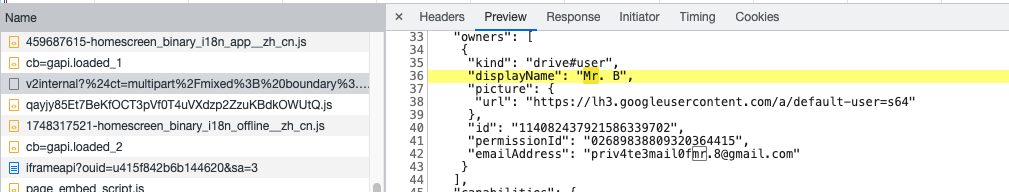
找到Gmail邮箱[email protected]
题目要求我们找到ProtonMail账号的PGP公钥,猜测邮箱前缀可能一样,即[email protected]
参照https://protonmail.com/support/knowledge-base/download-public-private-key/,下载PGP公钥
~$ wget https://api.protonmail.ch/pks/lookup?op=get&[email protected]
--2021-12-08 10:43:59-- https://api.protonmail.ch/pks/lookup?op=get&[email protected]
正在解析主机 api.protonmail.ch (api.protonmail.ch)... 185.70.42.25
正在连接 api.protonmail.ch (api.protonmail.ch)|185.70.42.25|:443... 已连接。
已发出 HTTP 请求,正在等待回应... 200 OK
长度:709 [application/pgp-keys]
正在保存至: “lookup?op=get&[email protected]”
lookup?op=get&search=priv4te3mail0fmr 100%[========================================================================>] 709 --.-KB/s 用时 0s
2021-12-08 10:44:00 (225 MB/s) - 已保存 “lookup?op=get&[email protected]” [709/709])
~$ cat lookup?op=get&[email protected]
-----BEGIN PGP PUBLIC KEY BLOCK-----
Version: ProtonMail
xjMEYZcIIhYJKwYBBAHaRw8BAQdAgXzkYJTBPtkxMSemLogafK1ryTzAsPoU
bjT8hQ6Wc4XNRXByaXY0dGUzbWFpbDBmbXIuOEBwcm90b25tYWlsLmNvbSA8
cHJpdjR0ZTNtYWlsMGZtci44QHByb3Rvbm1haWwuY29tPsKPBBAWCgAgBQJh
lwgiBgsJBwgDAgQVCAoCBBYCAQACGQECGwMCHgEAIQkQBcfjCjlf+3IWIQRS
LQS+kFOUoSEmSs4Fx+MKOV/7cgCtAP0dhlLk+UMY9FBnN/SiR+nIObn0q4f/
AS2k8kRvuA9cQgEA13kb1fTDmIGXp/rkTh9MSUt22m6rF5khiOr9yCYoTQrO
OARhlwgiEgorBgEEAZdVAQUBAQdARRDPDTZcD3gJkaXMzYOSGcLSY0M8PEMs
8w0eI9ydnxcDAQgHwngEGBYIAAkFAmGXCCICGwwAIQkQBcfjCjlf+3IWIQRS
LQS+kFOUoSEmSs4Fx+MKOV/7ckoLAQCjmVOWyFLflAz5dCinOZI0G8yOsduV
8PSw2hvTeyiZMwEAkl9U2tmg2i/XW5PckxqvNgxAZZkkEoQPWa6UpKICIw8=
=E+gi
-----END PGP PUBLIC KEY BLOCK-----
flag:SBCTF{xjMEYZcIIhYJKwYBBAHaRw8BAQdAgXzkYJTBPtkxMSemLogafK1ryTzAsPoUbjT8hQ6Wc4XNRXByaXY0dGUzbWFpbDBmbXIuOEBwcm90b25tYWlsLmNvbSA8cHJpdjR0ZTNtYWlsMGZtci44QHByb3Rvbm1haWwuY29tPsKPBBAWCgAgBQJhlwgiBgsJBwgDAgQVCAoCBBYCAQACGQECGwMCHgEAIQkQBcfjCjlf+3IWIQRSLQS+kFOUoSEmSs4Fx+MKOV/7cgCtAP0dhlLk+UMY9FBnN/SiR+nIObn0q4f/AS2k8kRvuA9cQgEA13kb1fTDmIGXp/rkTh9MSUt22m6rF5khiOr9yCYoTQrOOARhlwgiEgorBgEEAZdVAQUBAQdARRDPDTZcD3gJkaXMzYOSGcLSY0M8PEMs8w0eI9ydnxcDAQgHwngEGBYIAAkFAmGXCCICGwwAIQkQBcfjCjlf+3IWIQRSLQS+kFOUoSEmSs4Fx+MKOV/7ckoLAQCjmVOWyFLflAz5dCinOZI0G8yOsduV8PSw2hvTeyiZMwEAkl9U2tmg2i/XW5PckxqvNgxAZZkkEoQPWa6UpKICIw8==E+gi}
Tricks 1
A couple of PHP Tricks, give it a try.
<?php
error_reporting(0);
if (isset($_GET["a"]) && isset($_GET["b"])) {
if ($_GET["a"] !== $_GET["b"] && sha1($_GET["a"]) === sha1($_GET["b"])) {
if ($_GET["a"] !== $_GET["b"] && md5($_GET["a"]) === md5($_GET["b"])) {
$flag = file_get_contents("../../flag");
echo $flag;
}else {
echo "Didn't get passed MD5.";
}
}else {
echo "Didn't get passed SHA1.";
}
}else {
highlight_file(__FILE__);
die();
}
?>
md5和sha1 不能用来处理数组,md5(arr)和sha1(arr)会返回null
payload: a[]=a&b[]=b
~$ curl "https://ch5.sbug.se/?a[]=a&b[]=b"
SBCTF{g07_2_w17h_0n3_SH07?}
flag:SBCTF{g07_2_w17h_0n3_SH07?}
Tricks 2
Another round of PHP Tricks, good luck.
<?php error_reporting(0);
if (isset($_GET['a']) && isset($_GET['b'])) {
if ( strlen($_GET['a']) > mb_strlen($_GET['b'], base64_decode('dXRmOA==') )) {
if (strlen($_GET['b']) > mb_strlen($_GET['a'], base64_decode('dXRmOA=='))) {
$u327a6c4304ad5938 = file_get_contents(base64_decode('Li4vLi4vZmxhZw=='));
echo $u327a6c4304ad5938;
} else {
echo base64_decode('QWxyaWdodC4=');
}
} else {
echo base64_decode('VHJ5IGhhcmRlci4=');
}
} else {
highlight_file(__FILE__);
die();
} ?>
strlen返回的是字符串的字节数,而不是其中字符的数量.
mb-strlen 用来获取字符串的长度,多字节的字符被计为1.
因此这里用多字节字符作为参数即可
payload: a=大&b=大
$ curl "https://ch6.sbug.se/?a=大&b=大"
SBCTF{d1d_y0u_kn0w_abou7_7h47?}
flag:SBCTF{d1d_y0u_kn0w_abou7_7h47?}