Retro!
Our original logo was created in paint, I wonder what other secrets it hides?
题目给了一张图片:

使用exiftool工具查看图片元数据:
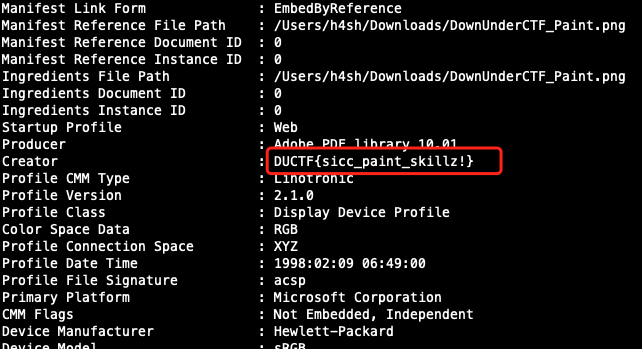
flag:DUCTF{sicc_paint_skillz!}
General Skills Quiz
QUIZ TIME! Just answer the questions. Pretty easy right?
Author: Crem
nc pwn-2021.duc.tf 31905
本题要求使用nc命令连接远程服务器,并在30s内回答所有问题.
代码:
from pwn import *
from urllib.parse import unquote
import base64
def rot13(message):
PAIRS = dict(zip("abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ",
"nopqrstuvwxyzabcdefghijklmNOPQRSTUVWXYZABCDEFGHIJKLM"))
return "".join(PAIRS.get(c, c) for c in message)
p = remote('pwn-2021.duc.tf', 31905)
p.send(b'\n')
p.recvuntil(b'ticking...', drop=True)
p.recvline()
while True:
s = p.recvline().decode('utf-8').strip('\n')
print(s)
t = s.split()[-1]
print(t)
if '1+1=?' in s:
p.send('2'.encode())
elif 'Decode this hex string and provide me the original number (base 10)' in s:
p.send(str(int(t, 16)).encode())
elif 'Decode this hex string and provide me the original ASCII letter' in s:
p.send(chr(int(t, 16)).encode())
elif 'Decode this URL encoded string and provide me the original ASCII symbols' in s:
p.send(unquote(t).encode())
elif 'Decode this base64 string and provide me the plaintext' in s:
p.send(base64.b64decode(t))
elif 'Encode this plaintext string and provide me the Base64' in s:
p.send(base64.b64encode(t.encode()))
elif 'Decode this rot13 string and provide me the plaintext' in s:
p.send(rot13(t).encode())
elif 'Encode this plaintext string and provide me the ROT13' in s:
p.send(rot13(t).encode())
elif 'Decode this binary string and provide me the original number' in s:
p.send(str(int(t, 2)).encode())
elif 'Encode this number and provide me the binary equivalent' in s:
p.send(bin(int(t)).encode())
else:
p.send('DUCTF\n'.encode())
print(p.recvall().decode())
break
p.send('\n'.encode())
p.recvline()
p.recvline()
flag:DUCTF{you_aced_the_quiz!_have_a_gold_star_champion}
Who goes there?
Disclaimer: Please note that this storyline, including any previous or future additions are all fictional and created solely for this challenge as part of DownUnder CTF. These are real places however they have no association/affiliation to the event, you are not required to call any place or make contact with anyone, doing so may disqualify you from the event.
Welcome to the team, glad you chose to join us - hopefully you’ll like it here and want to stay. Let me tell you about your first task:
We’ve observed an underground criminal RaaS operation calling back to this domain, can you find the number of the individual who registered the domain?
646f776e756e646572.xyz
题目给了我们一个域名,要求我们找到注册人的联系电话
在whois上搜索即可:
flag:DUCTF{+61.420091337}
no strings
This binary contains a free flag. No strings attached, seriously!
使用hexdump -C nostrings查看16进制:
00002000 01 00 02 00 00 00 00 00 44 00 55 00 43 00 54 00 |........D.U.C.T.|
00002010 46 00 7b 00 73 00 74 00 72 00 69 00 6e 00 67 00 |F.{.s.t.r.i.n.g.|
00002020 65 00 6e 00 74 00 5f 00 73 00 74 00 72 00 69 00 |e.n.t._.s.t.r.i.|
00002030 6e 00 67 00 73 00 5f 00 73 00 74 00 72 00 69 00 |n.g.s._.s.t.r.i.|
00002040 6e 00 67 00 7d 00 66 6c 61 67 3f 20 00 77 72 6f |n.g.}.flag? .wro|
00002050 6e 67 21 00 63 6f 72 72 65 63 74 21 00 00 00 00 |ng!.correct!....|
00002060 01 1b 03 3b 34 00 00 00 05 00 00 00 c0 ef ff ff |...;4...........|
00002070 68 00 00 00 20 f0 ff ff 50 00 00 00 19 f1 ff ff |h... ...P.......|
00002080 90 00 00 00 f0 f1 ff ff b8 00 00 00 60 f2 ff ff |............`...|
00002090 00 01 00 00 00 00 00 00 14 00 00 00 00 00 00 00 |................|
000020a0 01 7a 52 00 01 78 10 01 1b 0c 07 08 90 01 00 00 |.zR..x..........|
000020b0 14 00 00 00 1c 00 00 00 c8 ef ff ff 2f 00 00 00 |............/...|
000020c0 00 44 07 10 00 00 00 00 24 00 00 00 34 00 00 00 |.D......$...4...|
000020d0 50 ef ff ff 60 00 00 00 00 0e 10 46 0e 18 4a 0f |P...`......F..J.|
000020e0 0b 77 08 80 00 3f 1a 3b 2a 33 24 22 00 00 00 00 |.w...?.;*3$"....|
000020f0 24 00 00 00 5c 00 00 00 81 f0 ff ff d2 00 00 00 |$...\...........|
00002100 00 41 0e 10 86 02 43 0d 06 45 83 03 02 c8 0c 07 |.A....C..E......|
00002110 08 00 00 00 00 00 00 00 44 00 00 00 84 00 00 00 |........D.......|
00002120 30 f1 ff ff 65 00 00 00 00 46 0e 10 8f 02 49 0e |0...e....F....I.|
00002130 18 8e 03 45 0e 20 8d 04 45 0e 28 8c 05 44 0e 30 |...E. ..E.(..D.0|
00002140 86 06 48 0e 38 83 07 47 0e 40 6e 0e 38 41 0e 30 |[email protected]|
00002150 41 0e 28 42 0e 20 42 0e 18 42 0e 10 42 0e 08 00 |A.(B. B..B..B...|
00002160 10 00 00 00 cc 00 00 00 58 f1 ff ff 05 00 00 00 |........X.......|
00002170 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
flag:DUCTF{stringent_strings_string}